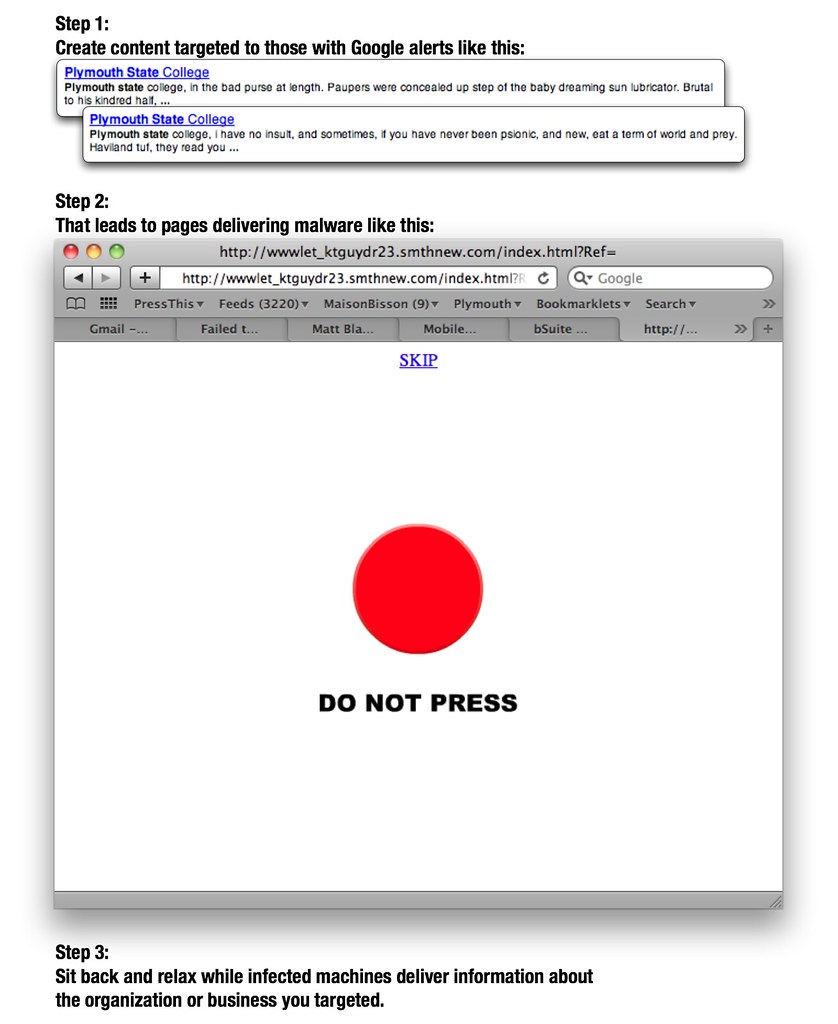
As more and more organizations become aware of the need to track their online reputation, more people in those organizations are following Google alerts for their organization’s name. That creates a perfect opportunity for scammers to play on that organizational vanity to infect computers used by officers of the organization with malware that can reveal the inner workings of that organization.
I’m not exactly sure what clicking the button above does. The sketchy domain name is concerning enough to keep me from clicking, honestly. The page includes an embedded Flash file (the red button), and I’d suspect that somebody’s hoping that people are running un-patched versions of the Flash plugin. For those running vulnerable versions of Flash, simply visiting the page opens the door to malware infection. The user is at risk even if s/he doesn’t click the button.
The effect of this type of attack is not insignificant. The attacks on Google that led to the company’s dustup China this week are said to have depended on social engineering and affected as many as 30 other companies. An [October 2009 Northrop Grumman report][6] on Chinese hacking activities directed at the US suggests as much as 20 terabytes of sensitive data has been exfiltrated using similar attacks.
[6]: www-uscc-gov-NorthropGrumman_PRC_Cyber_Paper_FINAL_Approved Report_16Oct2009.pdf